Introduction
Hello and welcome to the darknet markets bible for vendors. While the DNM bible for buyers aims to be a complete guide and walk-through for buyers, this is not the case for this bible. The following information will just be a help for already operating vendors or people who want to become one.
Being a successful DNM vendor is an extremely complex topic and is an ongoing job. There is much more information you need to gather before becoming a vendor than just reading the DNM vendor bible. If you do not want your vending career to end with your conviction, here are just a few points you have to consider:
- You have to know the ins and outs of the DNM buyer bible.
- You have to be aware of news in the DNM scene by following market forums and other discussion places. If someone posts valuable information about vending for example, you better take notes.
- You have to stay up to date on law enforcement actions, especially the ones that happen in your country.
- Know when your competitors get busted and why, know what method the customs use to check packages, know if there is an ongoing LE operation in your area that focuses on DNM vendors and many more actors.
- A tiny mistake can be enough for LE to throw your ass in jail. This is not an exaggeration, just one tiny mistake is enough for LE to catch you. Be it a partial fingerprint that you left when packaging, or an accidentally unencrypted message, LE will do everything to exploit every single mistake you make.
Moreover is vending a real job, not just a hobby. If you fuck up, you flush your life down the drain. You will most likely get jail time, spend thousands of dollars on a lawyer, get disowned by your family, get news articles about you being a drug dealer published, get a permanent record which will prevent you from getting jobs left and right in your entire future life.
If you can not deal with the consequences of getting caught, do not become a DNM vendor.
As you see, vending is not just something you start when getting bored or thinking it would be "cool". If you do not want to get caught,you do not even get to brag about what you are doing. Every person that knows about your operation and is not working for you, is one too many. Do not expect any real life fame from being a DNM vendor. And if you get some, you are doing it wrong.
There is also the common misconception that a DNM vendor makes fast and much money. This is utterly wrong. A DNM vendor will have to wait much longer till he actually gets to hold cash in his hands for the product he sells. A normal, offline dealer for example just meets up with the buyer, sells the gram of coke and gets the money in cash.
The DNM vendor however, has to check the buyer history and validate the address, then accept the order, package it without leaving any fingerprints or DNA traces, then use suitable transportation methods to drop the package off at strategic locations, then wait days till the buyer receives his order. If you are in luck, the buyer will not try to scam you and the package will go through without getting seized, so the buyer releases the bitcoins to you. Now you still have to exchange the bitcoins into actual dollars, and that is a whole topic itself because you need to break the link between the bitcoins you got through drug dealing and the ones you sell on the bitcoin exchange, you need to use cash-out methods that leave no or very little paper-trail (you will see later why this is crucial)...
All this is a pain in the ass and madly time consuming. So if you are not willing to go these many extra miles or not willing to deal with the technical side of being a DNM vendor (if you for example want to skip using Tails you can fuck right off), then stick to offline dealing. It is not a shame to admit that being a DNM vendor is too complicated or elaborate for you, because only a part of people reading this is actually ready to become a proper DNM vendor. If you want to make quick and easy money, go the traditional way of drug dealing.
Now that the "easy" part of being a DNM vendor is debunked, let's get to the "much money" part. You probably know a handful of kingpins that made a small fortune by selling on DNMs and some of them are still not caught. This gives some wanna-be vendors the false implications it will be the case for them too, which is wrong.
In fact many DNM vendors are just small time ones that make a couple of hundreds or a couple of thousands dollars profit and then stop vending. It is the silent majority you rarely hear about. And there is nothing wrong about that since you should expect to fall into that category too. While you are vending you will always have to keep in mind that it is better to leave the game as a free man and with some money you made, than getting busted with large amounts of drugs and money.
Many people do not know when to stop because they get blinded by the online fame and reputation they have. You will sooner or later read about them in news articles and court documents. Do not become one of them.
Please note that the DNM bible is only possible because a lot of awesome people dedicated countless hours of their free time to writing the tools you will use when following the guide. So please show your appreciation to them by making a donation to the Tor Project, Tails and/or GnuPG once in a while. If you have money to buy drugs, you also have money to reward the people who make it possible for you to order drugs safely to your front door.
Happy reading and stay safe.
General Tips
When getting asked if you provide alternative payment
methods (e.g. paypal) or other OpSec compromising
things, do not accuse the buyer of being law
enforcement and go on a long rant about the
government and drug laws. Instead give the user a
short refusal and do not waste much time on it.
No insults or accusations, keep it brief and
professional.
There is a limit for how long you should vend.
If you start vending it is only a matter of time till law enforcement puts you under investigation. How long that takes depends on several factors such as the product(s) you sell, your ability to fly under the radar (if you are a very extroverted vendor or keep it to yourself), your profile (if you indicate that your OpSec is shit, e.g. listing a phone number will attract law enforcement like flies to shit).
But sooner or later law enforcement is going to investigate you. You do not know when this is, so you have to stay cautions all the time, not just step up your OpSec after vending for some time. When this phase begins, it will solely depend on your OpSec, cleverness and creativeness how long it will take, as well how much resources law enforcement invests into getting your ass into jail. As you will read later on that page, there are great differences in how long the investigations take.
However, your goal is not to vend until you get busted. You need to quit while being ahead. If you want to vend for several years, you need to terminate your vendor accounts and start all over again several times. In general, no vendor should vend over 1,5 to 2 years.
This is a good time period to ensure that the investigation that law enforcement runs is not too much in progress (i.e. already observing your home) but you destroy the one that is already in progress and flush their month long work down the toilet. Then, if you still want to vendor, start all over with a new vendor identity and with following the tips below.
This is what you should aim for.
Yes, it is god damn time-consuming and shitty to start all over again and giving up your valuable reputation. Nobody likes to do it, but if you value your freedom you need to do it. All busted vendors have one thing in common: law enforcement had simply enough time to investigate them. If you are smart you do not do the same mistake, but switch vendor identities after 1,5 to 2 years.
If you do it right, you can vend for years and make insane money.
Sounds better than decades in jail because you could not say goodbye to your vendor reputation, doesn't it?
So since you now know why it is crucial to switch vendor accounts, here is what you need to keep in mind when doing so. Starting under a new vendor alias is much more than just creating a new account and start vending there. It would actually be counter-productive if you would do that since you would only loose your reputation and customers and law enforcement would still be able to easily connect the two vendor accounts.
You have to change many aspects in your vendor operation and your behavior in order to avoid law enforcement being able to draw the connection and therefore destroying all the effort you put into appearing as a new vendor. These aspects you have to change include for example:
- Your writing style. If you wrote like a 5th grader with your old account, you have to make the switch and for example behave and write like a professional businessman.
- The key size if your PGP key. If for example you used 2048 bit before, create a new 4096 bit one.
- The sort of your vendor name. That means if your old vendor name was "goodVendor", you should not call yourself "greatVendor" but rather something completely different, like "JohnSmith Inc".
- Your online times. If you logged into your vendor accounts every evening, it is now time to change these times.
- Your mail drops. Instead of going in the same area to drop off your packages, move in a completely different direction and drop them off there.
- The vendor persona. That means if you played a tight-lipped one-man vendor before, try acting like a vendor collective which for example mentions on their profile page how their operation is run by several people and has dedicated shippers.
- How you package the orders. That not only means using different package material but also changing your stealth and package layout.
- The time when you stop using your old account and start using your new one. That means, do not immediately start using the new account after you gave up the old one. Make a several month long break for example or operate both at the same time for a month or so (only recommended if you already have some experience and can strictly separate the two vendor identities).
There are many more aspects that you have to consider. The above are just to give you a general idea of what you have to remember. Keep in mind: if you only forget changing one, or fuck up changing one of those aspects, all your effort can be worthless. You definitely do not want that, so be systematic when changing your vendor identity.
It will not be easy to switch vendor identities, but it will be worth it.
Do not accept orders where the customer did not encrypt sensitive data (like his address) with PGP. This will not only improve the DNM scene as a whole by promoting better OpSec but also protect the buyer and yourself.
For example if the market gets seized LE will have his address and if you accept orders from such users they usually make other OpSec mistakes too and would be more than willing to tell LE everything when they get caught (buyers who confessed everything and even told LE from which vendor they ordered are not rare).
Keep as little bitcoins on the market as possible.
This is important for buyers but even more for vendors who deal with much larger sums. The past showed that vendors (other users of course too) often get scammed and lose their money, do not be one of them. Or at least make sure you lose as little money as possible by withdrawing your earned bitcoins immediately after the purchase was finalized.
Do not include any additional and unnecessary information in the packages that you sent. That means for example do not print your vendor name on the product you packaged, even if it is inside. It is useless (the buyer already knows that he made an order with you) and is a great help for law enforcement when they seize the package.
Manage your online times. That means do not log in right after you get home and do not go into vacation mode at the exact same dates as when you actually go into vacation in real life. It would not only be extremely incriminating when law enforcement is already observing you, but also when they compare the vacation data and login data (which are all public and get collected by law enforcement) with the suspects lives' they have. So add some delays and padding, for example only log in during specific parts of the day although you could access the markets more often.
Go into vacation for some days although you just continue your life as usual and if you actually go into vacation in real life, do not match these dates with your break on the DNMs.
Create an identity.
Create a character for yourself, build it and maintain it.
It also helps writing the characteristics of the identity down in a text file (of course stored on your persistence volume in Tails) so you do not accidentally leak your real persona.
A good relation with your customers is crucial, but don't turn into a vendor who can be scammed easily. Be fair and honest, but don't go around giving free reships or refunds after every complaint. You WILL get a ton of customers who are out there to score free drugs from you. Don't be afraid to take a negative feedback once in a while.
Source as many items offline as possible. That means do not order all your vending equipment from amazon, this already got a t least one vendor in jail as you should know from the General Tips chapter. Instead purchase as much of your needed equipment offline in stores and pay with cash. You really do not want your past mistakes and sloppiness to haunt you later in your vending career.
Keep your operation as small as possible. That means only add new workers if absolutely necessary. Every person that knows something about your operation is a risk. You can never erase or take back what you told someone (let's not talk about murder), so a confidant is a permanent risk to your freedom. Needless to say that nobody that is involved in your operation should know anything about it. The ones that are should be kept in the dark as much as possible.
Use the need-to-know principle: if they do not need to know something for doing their tasks, do not tell them it. Need a reason?
"Sadly, the fed’s #1 informant was XanaxKing’s friend of 15 years." (source).
And this is by far not the only case where vendors got betrayed by confidants: "The primary suspect’s girlfriend, reported in many articles the suspect’s "cohabitator,” texted her boss information about the operation. She said her boyfriend “operated a vast drug trafficking ring.”" (source).
Because of such retards, it is necessary to be extremely careful when adding new workers. It is best to do it all yourself, in the end you get more profit that way too.
Do not taunt law enforcement.
They are just doing their job and you do yours.
There is no reason for you to insult them or make fun of them by making reddit posts that provoke them by telling nobody will every catch you.
This is childish behavior.
Be mature and keep it professional.
Not sure what to sell?
Only three things matter. Firstly, the quality. And after that, the only two factors are how much you pay for it and how much you charge for it.
The most profitable substance is the substance that you can get for the best quality for the best price, as long as you can pass those savings on to your customers. If you plan on being a vendor, the dark net enables sellers of even some pretty obscure drugs to find a huge market.
My point is that no matter what drug you sell, if you have the highest quality and the best price your product sells itself and you will make more money than you ever dreamed you would, as long as you have a steady supply. again.... doesn't matter what drug it is. (source)
Read up the laws that you are breaking.
Seriously.
By just investing a few hours into this, you can easily reduce your future sentence up to several years!
There are common pitfalls which you should be aware of that can easily increase your sentence, even if you do not find it fair of would think of it as a factor that would increase your sentence.
There were countless people before you, that are in the same or similar situation as you are now so it is not unknown legal territory.
The tips are there.
Read them!
As you will learn in the What not to do chapter, there are great differences how long the law enforcement investigations take.
They can take only one month (for the vendor BTH-Overdose) but can also go over 20 months (for the vendor Hedon).
So you goal is not to hope that law enforcement will not invest much into your investigation, but to make it the job of the investigating agents as hard as possible.
Do not give them as less information as possible and keep your OpSec tight at all times. If you then also try your best to fly under the radar (by not being overly active on forums and not taunting law enforcement), you can greatly increase the length of an investigation.
Remember: you goal is not to vend as long as possible, but to quit while you are ahead.
Find a good place, or several ones, where to store the majority of your product. It is absolutely deadly to store it all in your house or other properties associated with your name, because this is the first place law enforcement will look. And trust me, if there is something hidden, they will find it. Here some discussion about stashes, make sure you read it.
You will have leftovers from your packaging or other stuff that is vending related.
Do not put that in the garbage.
It already costed several vendor their freedom.
Just one example:
In August 2016, DEA agents recovered pieces of evidence from Heady Warez’s trash, including “26 pieces of paper with various handwritten acronyms, colors and numbers, such as ‘10 yellow Benz,’ ‘85 Xan,’ ‘10 OC 40 orange,’ ‘6 D&G,’” which closely resembled online drug listings posted by “USTOUS” for benzodiazepine and alprazolam, both psychoactive drugs, and oxycodone, Infante wrote.
(source)
It is crucial that you destroy all that potential evidence.
It is best to burn it, throwing it away in other trashcans that are not linked to you may work too but then the trash should not be usable for law enforcement (i.e. shred paper for example).
Make sure your product is tested.
A popular vendor a few years ago sent out pounds of sugar without realizing. Some people send out analogues without realizing.
Some people press/lay their own product and send out bunks without realizing. For the sake of customers and reship/refund costs, test your product.
Use 2-Factor Authentication.
There are no excuses fro not doing so.
Do not scam.
You already have law enforcement hunting you so that last thing you need is angry customers who know details about your packaging, stealth...
Some vendors have made a practice of overwriting comments on a periodic or as-needed basis (for example on reddit).
This seems to be driven by an intent to complicate retrospective information gathering, but is largely ineffectual. There are trivially simple-to-use tools that can circumvent this practice, and it should not be part of any vendors' or buyers' OpSec strategy.
You should always assume that as soon as you submit a comment or post, it will be stored forever. The same goes for any other information that you transmit to websites.
For a tangible example, try this link: http://apiv2.pushshift.io/reddit/comment/fetch/?author=%5bRedditUsernameWithoutBrackets%5d&limit=500&sort=dsc
Delete one of your recent comments, and see if the full text is still available.
Nothing said reddit or on any other forum can be scrubbed. If a past statement compromises OpSec, the appropriate response is to burn the account and start fresh, not attempt a half-assed redaction.
As a vendor, you do not always have the luxury of being able to mitigate past mistakes by starting over with a new account, so think before you write.
What Not To Do
There are many DNM vendors who got busted and there will be many more.To avoid being one of them, you will have to read about them, analyze what they did wrong and then take counter measures to avoid doing the same mistakes.
A bad vendor does not learn from his mistakes, a normal vendor learns from his mistakes but a good vendor learns from the mistakes of other vendors.
Summary #1
Summary of 6 vendor busts: what they did wrong
There are many reports and articles on dnm vendors getting busted, but it is not always easy to find valueable information about the bust and what led to it. In order to provide a safer dnm experience for everyone I will post a summary of 6 busts which contain things that the vendors did wrong and gave law enforcement and advantage and things that they did right which disrupted the investigations.
To vendors reading this: please take 5 minutes of your time to read the summaries and make sure that you are not doing the same mistakes that your competition did. Also I know some of you have already collected information about vendor busts and I am asking you to share it with the community here to make the dnms a bit safer.
Bust #1.1: Alexandrus
sources:
http://fokus.dn.se/alexandrus/ [english: https://translate.google.com/translate?hl=en&sl=sv&tl=en&u=http%3A%2F%2Ffokus.dn.se%2Falexandrus%2F]
http://norran.se/nyheter/blaljus-nyheter/harifran-skotte-han-storstanarkotikaligan408757 [english: https://translate.google.com/translate?sl=auto&tl=en&js=y&prev=_t&hl=en&ie=UTF8&u=http%3A%2F%2Fnorran.se%2Fnyheter%2Fblaljusnyheter%2Fharifran-skotte-han-storsta-narkotikaligan-408757&edittext=]
notes:
- continued to vend under the same alias after SR got seized, his data was handed to Swedish LE by the FBI
- selling unique products in his country [no other vendors who sold cannabis edibles in Sweden]
- no job, might be suspicious although he had no criminal record
- didn't pulled the Tails USB stick out when the raid took place → be always in the same room when you have booted Tails
- use many different mailboxes [he used 60]
- keep the packaging area clean [no DNA]
- use a printer for the destination and return addresses, use real return addresses but they shouldn't report the letter to LE if it is mailed back to the return address [i.e. drug house instead of a company address]
- LE monitored only the most strategic mailboxes, not all 60
- when he delivered the letters to a monitored mailbox, LE got his name because he drove there with his car
- LE opened the mailbox right after he left and took out the letters he sent, but let the letters go through [329 letters in total] → no warning signs for the vendor that he was being monitored
- LE made test purchases from the vendor and found that he sent drugs to the test purchase address after they opened the mailbox again → maybe only accept buyers with a history after some time
- Vendor was watched by LE out of cars parked near the mailboxes
- Vendor had the latest issue of the Narcotics Officers Association's magazine → stay informed about LEs tricks
Bust #1.2: Area51 a.k.a Darkapollo
sources:
discussion link: https://www.reddit.com/r/DarkNetMarkets/comments/4y34cp/step_by_step_dissection_of_a_darknet_vendor_bust/
timeline: https://www.deepdotweb.com/2016/08/26/timeline-arrestsalphabay-vendors-area51-darkapollo/
notes:
- both vendors had their PGP keys registered to same email address
- they used this email address on social media accounts linked to their real name
- LEOs made two orders and a drug and fingerprint analysis showed the fingerprints of one suspect on both packages (on the Mylar and USPS envelope)
- LEOs did a comparative analysis with the already gained information to identify who purchased the postage:
- they were able to identify the time, date, and location the postage was purchased via the Postage Validation Imprinter (PVI) label
- postage for parcel #1 was purchased via an SSK (Self Service Kiosk) located near the residences of both suspectsb
- PVI labels were bought with the same credit card → LEOs were able to identify additional postage being purchased utilizing the same card number
- photos are taken during each SSK transaction → LEOs identified one of the suspects
- vendor(s) used the same return address for both undercover purchases and one intercepted parcel, probably for many other ones too
- the intercepted parcel was probably detected because LEOs searched the mailcover database for the return address used for the two undercover purchases → switch return addresses regulary
- vendors were already part of an investigation because they also sold their products near their residences in real life
Bust #1.3: CaliConnect
sources:
http://arstechnica.com/tech-policy/2016/08/if-youre-an-alleged-drugdealer-dont-use-asshole209-as-a-password/
notes:
- used the same account on several markets over a long period of time → strong case for LE
- weak PGP password (“asshole209” with 209 being his area code)
- LE installed a GPS tracking device on his car with a search warrant
- trademarked his own vendor name using his real name
- used post offices near his home to ship his packages
- he accepted non-bitcoin payments in the past which had his identity tied to them
- kept incriminating things at his home: numerous items associated with the distribution of narcotics, including anti-static bags, a digital scale, food saver vacuum sealing bags; Amazon boxes with plastic storage bags; a trash bag containing marijuana, a box containing a sealed bag of marijuana, also pieces of clothing apparel with the label 'caliconnect'
- allowed law enforcement to search his nearby storage units → do not consent to searches or seizures
- told agents who questioned him that he traded bitcoins
- he and his SO had no job for 6 years but could still pay all the bills
- found unencrypted things associated to the CaliConnect profile: the black and gold 'Caliconnect' logo in use on AlphaBay, an installation of Tor, and a decrypted message that matched, identically, the controlled Buffalo, New York, transaction
Bust #1.4: Owlcity
sources:
https://archive.li/o/ufVKO/https:/www.reddit.com/r/DarkNetMarkets/comments/4vw1f7/alphabay_seller_owlcity_arrested_due_to_checking/
notes:
- used no protection for looking up tracking numbers → use a VPN [not Tor because it is too suspicous] or a third party tracking website
- LE began in-person surveillance of Leslie [owner of the wifi from which the tracking number was checked] → watched him drive to the post office with additional orders and intercepted the packages
- ISP monitoring of Tor activity, correlation of Owlcity inactivity with computer repair
Bust #1.5: Pfandleiher
sources:
https://archive.li/o/ufVKO/https:/web.archive.org/web/20160317052841/http:/www.zeit.de/2014/12/drogenhandel-silk-road-pfandleiher and https://archive.li/o/ufVKO/https:/web.archive.org/web/20160317052819/http:/www.zeit.de/2014/12/drogenhandel-silk-road-pfandleiher/seite-2 [no
direct translation link available, please copy the
text from the article and
manually enter it into a translator]
notes:
- was jobless and drug addicted but also lived a lavish lifestyle
- investigation started after one wrong delivered package and a tip
- LE monitored the suspect over months
Bust #1.6: Shiny Flakes
sources:
https://archive.li/o/ufVKO/https:/web.archive.org/web/20160310112332/http:/motherboard.vice.com/read/the-rise-and-fall-of-shiny-flakes-germanys-online-drug-market
https://archive.li/o/ufVKO/www.nbcnews.com/news/world/germany-drug-bust-finds-4m-haul-destined-online-sale-cops-n322146
https://archive.li/o/ufVKO/https:/www.gwern.net/Black-market arrests
notes:
- investigation was sparked by an undelivered package which was opened for insufficient postage bouncing to the fake return addresses
- lead to profiling of his packages, tracing them back through the postal system, surveillance of package stations and him mailing them, and finally undercover buys & seizures of additional packages
- had not purged his customers’ data, and in conjunction with the profiling and intercepting of sent packages, this led to a reported total of “38 locations were searched and five other individuals were arrested” on 2015-03-10
- had a clearnet site
- operated from his home
Summary #2
https://archive.li/o/miHWy/https:/www.reddit.com/r/DarkNetMarkets/comments/5hftrt/summary_of_4_more_vendor_busts_what_they_did_wrong/
Since my previous post [https://www.reddit.com/r/DarkNetMarkets/comments/5ephb0/summary_of_6_vendor_busts_what_they_did_wrong/] was well received by the community here I decided to do a second part.Unfortunately this post is not as elaborate as the first one because I already summarized the most interesting and most documented ones in the first part.
Nevertheless it is worth reading if you are a vendor or just a curious buyer.
Before I start with the summaries I want to mention three points that came up during my research:
- Never use business addresses as return addresses. After reading through many cases I noticed that law enforcement only got involved into them because businesses received mail containing drugs [that they obviously did not send] and alerted them. Vendors that got investigated and eventually busted because of that are: Italian Mafia Brussels, Dr. Xanax, Evilution [just to name a few]. Although the business return address might make the packages less suspicious and more likely to get through customs it will backfire much harder when it gets returned to the alleged sender. Since the business is legit and does not want to get into trouble, the employees will always report the returned packages.
- Never trust anyone. The sentence gets thrown around a lot but it is worth repeating because if you are committing a crime with someone else, this person will always be a security risk and if law enforcement puts him under enough pressure he will sooner or later snitch on you. A dnm related example: XanaxKing's friend of 15 years became the most valuable informant in his case. Therefore your goal should be to involve as little people as possible in your operation and do not give them more information than you have to [the less they know the less the can tell law enforcement].
- Quantik posted some information about the Dr. Xanax case some time ago and included a link to an audio recording where law enforcement explained in court how they busted Dr. Xanax. Although I have the link [https://infotomb.com/i2iba] , infotomb is offline since quite some time now. Therefore I want to ask the community here if anyone downloaded it or summarized the content of it.
In order to provide a safer dnm experience for everyone I will post a summary of 4 busts which contain things that the vendors did wrong and gave law enforcement and advantage and things that they did right which disrupted the investigations.
Bust #2.1: Dr. Xanax
sources:
https://archive.li/o/miHWy/https:/www.deepdotweb.com/2015/10/23/quantikxanax-releases-intel-from-drxanax-bust/
https://archive.li/o/miHWy/https:/www.deepdotweb.com/2015/10/13/dnm-vendor-dr-xanax-busted/
notes:
- used a supplement shop which contacted local law enforcement because of the returned packages they received
- with the tracking of the packages that got returned law enforcement got a video of the guy who posted it
- postal workers were asked to look out for this guy → when someone recognized him he asked another postal employee to check the car ID
- law enforcement then seized all the packages over the next 9 days, followed him, bugged his car, and found the remaining infrastructure
- he only used 17 different post offices to drop off the packages [thanks to /u/CoXan for the tip]
Bust #2.2: ErKran
discussion link:
https://archive.li/o/miHWy/https:/www.reddit.com/r/DarkNetMarkets/comments/4t47d2/swedens_biggest_vendor_busted/
sources:
https://archive.li/o/miHWy/https:/www.deepdotweb.com/2016/07/21/swedens-largest-darknet-vendor-busted-authorities/
https://archive.li/o/miHWy/https:/translate.google.com/translate?sl=auto&tl=en&js=y&prev=_t&hl=en&ie=UTF-8&u=http%3A%2F%2Fwww.sydsvenskan.se%2F2016-07-15%2Fatal-for-storskalig-narkotikahandel&edit-text=&act=url
notes:
- sourced his products in bulk and internationally → customs seized one of the packages and investigation started because of the large amount
- investigation revealed many other packages addressed to non-existent companies in his town, he picked them up there
- most used addressed were put under surveillance → quick arrest
- he carried a handgun, cash and some drugs while picking up the package
- he probably talked and revealed another member of his group who gave away the warehouse that served as the vendor headquarter
- computers revealed that the group was vending on dnms and how many transactions they made; would not be the case if they used tails
- one of the guys had a stash [apparently a small pump house] in the forest which was found by school kids → teacher informed police but they could not find a suspect at the time → police now has a suspect in that case because of the ErKran bust
Bust #2.3: Evilution
sources:
https://archive.li/o/miHWy/https:/www.deepdotweb.com/2016/11/04/belgian-amphetamine-vendor-arrested-due-to-insufficient-postage-on-his-packages/
https://archive.li/o/miHWy/https:/web.archive.org/web/20161027134259/http:/kw.knack.be/west-vlaanderen/nieuws/criminaliteit/twintiger-uit-torhout-dealde-wereldwijd-synthetische-drugs-via-de-onderwereld-van-het-internet/article-normal-239819.html [google translator
not working for
the URL, copy the text manually and paste it into the
google translator]
notes:
- at least six packages got returned to sender because of insufficient postage
- he always used the same return address [a local computer shop], owner of the shop naturally contacted the police → investigation started
- police analyzed the returned packages → discovered fingerprints → vendor was already arrested previously → law enforcement got a name to the prints
- vendor had 4000 bitcoins at the time of the bust, he received most of them through legal programming jobs but now it is difficult to determine which bitcoins originated from drug dealing → do not mix legal bitcoins with illegal obtained ones
Bust #2.4: HollandOnline
discussion link:
https://archive.li/o/miHWy/https:/www.reddit.com/r/AgMarketplace/comments/2ywpkv/vendor_busted/ archived version with some of the deleted comments: https://archive.li/o/miHWy/https:/web.archive.org/web/20150314112159/http:/www.reddit.com/r/AgMarketplace/comments/2ywpkv/vendor_busted
sources:
https://archive.li/o/miHWy/https:/www.deepdotweb.com/2015/03/12/dutch-vendor-bust-hollandonline/
https://archive.li/o/miHWy/https:/web.archive.org/web/20160325231658/https:/www.om.nl/actueel/nieuwsberichten/@88570/aanhoudingen/ [google
translator not
working for the URL, copy the text manually and paste it
into the google
translator]
notes:
- random police officer witnessed a suspicious transaction where someone moved transported goods from the trunk of one car to another → got arrested
- the arrested man was already on law enforcement's radar because he was suspected to operate, amongst others, the vendor account HollandOnline
- sold on Silk Road 1, 2 and Agora under the same alias → vendor already was heavily on law enforcement's radar
- bitcoins seized → bad opsec setup
- another group member was only 20 years old at the time of the bust → missing life experience and online fame led to operating under the same alias and ultimately his arrest
That is it for now, if you know other busts that could
provide useful
information or additions to the summarized ones please
leave a
comment here.
One last shameless self-promotion: I developed an Addon
for Firefox
[also compatible with the Tor browser] which lets you
view selfposts of
NSFW subs [like this one] without having to enable
JavaScript. The
source code is of course publicly available, so check it
out if you want to
boost your
opsec: https://archive.li/o/miHWy/https:/www.reddit.com/r/DarkNetMarkets/comments/5ek0lm/a_present_for_the_lurkers_on_here/
Summary #3
2 more juicy vendor busts and what they did wrongOver the holidays I found time to go through more than 100 pages of criminal complaints, indictments and other resources that described how the vendors Blime-Sub (a.k.a. BTH-Overdose) and CaliGirl got busted. Now what is different compared to the first two parts [#1 and #2] is that these two cases are described in great detail and walk the reader through the entire investigation step-by-step.
Since they are quite lengthy I outlined the important parts of the investigation and wrote down the mistakes that the vendors did which eventually led to their bust. While the Blime-Sub bust is quite fresh [just 2 months ago], the CaliGirl case dates back to the good old SR days. However it is one of the best documented ones and many of the investigation techniques are still used today. In this edition we have some classic pitfalls like getting identified while buying the postage or leaving a detailed money trail but also some new ones, that have not been mentioned in the previous two parts.
I strongly encourage every vendor to read through these notes and analyse their own operation so they do not make the same mistakes that their colleagues/competition did. In the end it is not only your own future that is at risk but also the one of your customers.
Please read the whole post because it not only includes stupid vendor mistakes that you probably would never make, but also some tricky pitfalls which you would miss out if you just skim the post.
Before I come to the busts themselves I want to briefly talk about some aspects that are so important that I think they deserve a specific mention:
- If there is one thing the government does not fuck around with, it is money. For example the CaliGirl complaint contained over a dozen sites that went over every single cent the vendor ever received or deposited into his bank accounts. Every single company, from Wells Fargo to Western Union and MoneyGram, had extremely detailed records about where every cent came from and where it went, as well as IP addresses, log-in times, locations of used ATMs... This shows that vendors should avoid banks and wire transfer services whenever possible, because they all keep records and once they hand these over to law enforcement you are absolutely fucked.
- Know your limit. Many vendors just keep vending under the same name for years as if law enforcement is not interested in them. However what all these busts have in common is that law enforcement simply had enough time to investigate the vendors. So vendors remember to take a break once in a while and enjoy the reward of your hard work instead of ruining everything you have worked for in the past years by vending until you get busted. Better quit with some nice extra cash and your freedom than ending up in one of these summaries below.
- Law enforcement not only analyzes the content of seized packages but also the package itself. That means they look for any traces you may have left, for example fingerprints. This has proven to be useful and already led to arrests, just take a look at the Area51/Darkapollo or Blime-Sub/BTH-Overdose busts. So vendors should avoid leaving any fingerprints or DNA traces on and in the package because it not only allows to check if a suspect is the wanted vendor but can also reveal for example the eye and hair color of the person that left the DNA [http://www.medicaldaily.com/DNA-test-can-reveal-hair-eye-color-humans-living-800-years-ago-244266]. That would give law enforcement a big advantage when they stake out mail boxes. Here a really simple guide on how to remove these traces: http://biononymous.me/wp-content/uploads/2016/09/Tabloid-BiononymousGuide.jpg
Bust #3.1: CaliGirl [Matthew Jones]
sources:
https://archive.li/o/a7TKl/https:/www.justice.gov/sites/default/files/usao-mdfl/legacy/2014/05/30/20140530_Jones_Complaint.pdf
https://archive.li/o/a7TKl/https:/www.reddit.com/r/DarkNetMarkets/comments/2c2i3f/caligirl_criminal_complaint_excerpts/
notes:
- one involved Task Force Agent [TF agent in the following] even has "additional advanced training and epxerience in Computer Networking and Unix Systems Administration" → that was 3 years ago, imagine how many resources they put into dnm vendor investigations nowadays
- vendor used an alias similar to his real name [Matthew Jones]: Mateo Jones
- CaliGirl was among the top 5% of all vendors operating on SR → high profile
- law enforcement made 2 undercover purchases on SR and 6 off-site [all between July 2013 and March 2014]
- law enforcement was able to indetifiy what products he sold how often and his total sales volume because SR provided a detailed public record of it → do not use markets that do not obfuscate this information
- although CaliGirl used many different return addresses some of them were handwritten and some were business addresses [not a smart idea, see part 2], plus the tracking number revealed where the packages were shipped from
- for his fifth purchase the TF agent placed the order on January 3, 2014 but requested that it should not be shipped until January 23 [this could be a potential red flag for other vendors] → the TF agent then had time to go to the mail processing plant that handled most of the previous undercover packages and attempted to profile additional packages that matched packages sent by CaliGirl
- they found and seized 4 matching packages which originated from one mail collection box half a mile from Jones's residence away, all 4 packages had the same return address and one of it was the undercover order
- on January 13, 2014, the TF agent opened a suspicious package [taped excessively] that was sent to one of Jones's drops [where he received the products that he resold under the CaliGirl account], it contained almost 700 Hydrocodone tablets and was addresses to "Tyler Zeddai"
- CaliGirl offered the TF agent a special deal for Hydrocodone tablets and also sent him information about them [a link to a pill identification website] → the branding and picture supplied by CaliGirl matched the seized tablets on January 13 → the TF agent made the purchase
- for his next undercover order [undercover purchase #8] the TF agent claimed to be short on bitcoins and CaliGirl provided him with a contact [name, telephone number and local bitcoins username] that could sell him bitcoins for cash → that contact [Jones] was CaliGirl himself
- apparently the TF agent told Jones [when they talked about purchasing bitcoins] that he wanted to provide him with $1k to convert into bitcoins and then transfer the coins to CaliGirl [Jones should transfer the coins to CaliGirl not the TF agent] → indication that Jones at least knew CaliGirl [because Jones knew CaliGirl well enough to send him the coins]
- after the bitcoin purchase from Jones [$952, because Jones took a commision] the TF agent contacted CaliGirl about the order → CaliGirl said that it had already been shipped and the $1k were credited towards the purchase → further indication that Jones and CaliGirl are somehow connected
- the phone number that CaliGirl gave to the TF agent to contact Jones in order to buy bitcoins was purchased on Jones name one minute before CaliGirl mentioned it in his message → further indication that CaliGirl was probably Jones
- the features of the packages that CaliGirl sent which remained consistent included: the manner in which the sender and recipient addresses were printed and affixed, the placement and method of postage, and the type of envelope utilized → made packe profiling easier
- the postage used for the purchase mentioned above was an Automated Postal Center [APC] computer generated postage stamp → the TF agent was able to get the purchase date and location of the machine that was used to buy the postage
- since the machine stored images of the persons that used it, he was also able to get an image of the person who bought the postage in question - > compared this image to known images of Jones [including publically available images on facebook] → matched
- postage was paid for by the utilization of $5.00+ face-value stamps and the tracking numbers were affixed prior to mailing for every package → he did not have to pass the packages over a post office counter where he could get identified by postal staff or video surveillance systems → however he fucked up with the package sent on March 18, 2014 which had APC printed postage
- he used the same return address for every package but switched it once every week → this and other mistakes allowed detailed package profiling which made it possible for law enforcement to indentify a total of 135 packages sent by Jones → package profiling is a great threat so take counter measures
- some return addresses that CaliGirl used were connected to his real indentity [Matthew Jones]: e.g. a Hotel address were he stayed or a company which he owned → do not do that
- Jones' P.O. box [where he received his products which he resold] was opened under his name and "Tyler Zeddai" → all incoming mail was addressed to Tyler Zeddai but always picked up by Jones or his spouse - > manager found that suspicious [he did not contact law enforcement but when the TF agent interviewed him he was very talkative → maybe avoid P.O. boxes from "EZ Mail Services"]
- vendors: if you have to use P.O. boxes switch them once in a while [and use different companies] so it is more difficult for law enforcement to uncover the whole scope of your operation. also do not use these addresses for other purposes like opening bank accounts, which Jones did.
- the TF agent also reviewed records obtained from amazon about Jones' purchases which included purchase, shipping, billing, and IP address information → he bought zip lock baggies and bubble mailer manila envelopes which were also used for shipping the undercover purchases → do not order your shipping equipment online or at least not with your identity
- he also travelled to Colombia frequently → the TF agent compared these dates with the times when CaliGirl was on vacation → matched → vendors should go to fake vacations [vacation mode on the market but continuing their everyday life] and extended vactions [do not go into/come back from vaction on the exact days when you actually go away/come back]
- Note: Jones bought Oxycodone and Hydrocodone in Colombia and shipped them to the P.O. box mentioned above: it is easier and cheaper to get these products in Colombia and they are marked like many other tablets → careful inspection or laboratory anaylsis needed to indentify them → preferred by drug traffickers
- Xoom [an online wire transfer service where he had an account with his real data] revealed that he transferred over $58k from January 2012 to August 2013 to Colombia
- some of these transfers were sent to "Mateo Jones" which is an alias utilized by Matthew Jones on facebook → please learn to separate identities properly
- transactions have been structured in a manner to intentionally avoid triggering money laundering and reporting requirements [e.g. multiple transaction on the same day to the same person] → say hello to another charge
- he should have taken the money in cash with him on the plane or mail it to Colombia instead of producing all the detailed evidence by using Xoom
- "The Wells Fargo counter and ATM deposits [to one of Jones' accounts] were in inconsistent amounts, occurred on a variety of dates, and were made at a variety of geographical areas. Based on my training and experience, this activity is consistent with Bitcoin sales where a Bitcoin customer makes a pre-arranged counter-deposit into a Bitcoin dealer's bank account. The deposit slips contain only the minimum amount of information required to make a cash deposit. Based on my training, experience, and this investigation, this is common behavior utilized by Bitcoin exchangers and drug traffickers a when utilizing counter deposits to transmit currency." this was written 3 years ago, vendors should finally start using methods that do not create extensive and suspicious paper trails to cash out their bitcoins
- he used small variations in telephone numbers, addresses and other identifying information for receiving funds in his Western Union account → this is a common method drug traffickers and money launderers utilize to avoid detection by law enforcement → do not do this
- Jones used only one account on the exchanges [local bitcoins and and bitcoin-otc] to cash out his bitcoins for his entire vending time and also publicly linked the accounts on both sites
- 'fun' fact: a screen shot [exhibit 1] shows that law enforcement does not even disables javascript globally and seems to be using windows → they really need to step up their opsec :)
Bust #3.2: Blime-Sub a.k.a. BTH-Overdose
sources:
https://archive.li/o/a7TKl/https:/www.justice.gov/usao-edca/pr/fentanyl-and-heroin-sold-dark-web-marketplace
https://archive.li/o/a7TKl/https:/www.justice.gov/usao-edca/press-release/file/918811/download
discussion link:
https://archive.li/o/a7TKl/https:/www.reddit.com/r/DarkNetMarkets/comments/5imn2j/blimesub_arrested_according_to_press_release/
I also wrote an article on deepdotweb about this bust
using these notes,
so if you read it you can skip the following
notes. /u/deepdotdeepdotweb.com can you please post a
short
'confirmed' comment so that people know that I am not
bullshitting?
notes:
- after getting training on how to use dnms a DEA agent began analyzing and investigating top heroin vendors on alphabay in january 2016
- he initiated a full investigation into the vendors Blime-Sub and BTH- Overdose in september 2016
- he knew they were shipping from the west coast (possibly somewhere in california) because customers mentioned it in forums
- BTH-Overdose (Emil Babadjov) used the same email address for his pgp key as he used for his facebook account with his real name (but written backwards)
- Babadjov made a public facebook post in september 2015 that people could contact him through the email address he also used for his pgp keys
- on November 14th, 2016, the agent sent a subpoena to coinbase to get any information they have about the email address
- he received replies from Coinbase on the very same day and one day after:
- the email address was used to create an account in November 2015 for "Emil Babadjov"
- on March 18, 2016, he attempted to create another account with the name "Emil Babadjov" and the email address "blimesub@***.com" → do not mix vendor identities with exchange accounts and do not use vendor email addresses for any other purpose than talking to customers
- on November 14th, 2016, the agent got Babadjov's address (through his drivers license) and found out that he was arrested in 2013 for possession of controlled substances (but the charge was dismissed)
- on October 19, 2016, the agent bought $800 worth of bitcoins to buy 3g heroin on the next day from Blime-Sub on alphabay
- the parcel (UC parcel #1) arrived on October 25 at the undercover address and he got the return address and tracking number of it
- the product in the package was submitted to the DEA western regional lab for fingerprint and drug analysis after it got tested positive for heroin
- the agent got a response from the lab on November 10, 2016, which stated that it was a mix of heroin and fentanyl
- the US postal inspector was able to conduct comparative analysis of these parcels to identify who purchased the postage for UC parcel #1
- due to the Postage Validation Imprinter (PVI) the US postal inspector was able to see that the postage was bought on september 18 2016 at 4:03 PM via a Self-Service Kiosk (SSK) 0.7 miles away from Babadjov's known address
- the US postal inspector gave the photo that was taken by the SSK system during the transaction to the agent
- he identified the person in the photo as Emil Babadjov according to the drivers license and social media photos of Babadjov
- on November 16, 2016, the agent received another response from the DEA western regional lab that stated that two fingerprints belonging to Babadjov were found on the exterior of UC parcel #1
That is it for now, if you know other busts that could
provide useful
information or additions to the summarized ones please
leave a
comment here.
One last shameless self-promotion: I developed an Addon
for Firefox
[also compatible with the Tor browser] which lets you
view selfposts of
NSFW subs [like this one] without having to enable
JavaScript. The
source code is of course publicly available, so check it
out if you want to
boost your
opsec: https://archive.li/o/a7TKl/https:/www.reddit.com/r/DarkNetMarkets/comments/5ek0lm/a_present_for_the_lurkers_on_here/
Summary #4
Here is a ( list ) of many DNM arrest, pay especially close attention to the busts that involved vendors that sold the same product as you or were located in your country. But this is by far not enough, you will have to constantly watch out for new vendor busts and check what they did wrong.Setup
This chapter is about the technical side of your vendor operation.Luckily you just have to follow the instructions in the DNM Buyer Bible to set up Tails, learn how to use it. how to chose a market... Make sure you actually read every chapter since you have to know how a buyer will behave and what will set off red flags for him.
This is crucial and if you for example do not set up Tails you already fucked up. There is not excuse for a vendor to not use Tails.
Important: when choosing a printer, you have to make sure it works with Tails. If it does not you are compromising your own OpSec and risk getting yourself in jail just because of that one part of your setup. Handling customer's addresses is not something you should take lightly, always make sure that the information does not leave Tails (obviously other than on a paper printed by the printer). For more information about specific printers check this thread.
Before you start, make sure you also read this discussion so you know what you can expect when you are starting to vend.
-- BACK-UP YOUR DATA! --
You must must must have at least 2 copies of your persistence data. It is extremely easy to do and only takes a few minutes. You're fucked if your PGP keys, passwords and Bitcoin wallets disappear.
Tip: when setting up your electrum wallet on Tails, you can start the wallet creation process several times till you get a seed that you can remember better (e.g. because the word order makes more sense and is easier to remember).
Please also keep in mind that in some countries, law enforcement can force you to reveal your password and therefore incriminate yourself. You need to do your own research about the situation in your country regarding this topic.
To avoid loosing your bitcoins because of that, you could have a wallet which you rarely use but holds the majority of your funds. The only trace of it is the seed that you remember in your head. That way nobody can prove that you own more than the bitcoins in your usual vendor wallet (the one that you frequently use). That means you could be forced to give out your Tails password but they would only see your frequent wallet in electrum. If you want to access that big wallet just restore it from seed and delete it again when you are done. If you do that, make damn sure you do not forget that seed.
Alternatively you can create that wallet on an offline, non-persistent Tails, then save the seed on a flash drive and dig a hole for it in the desert. To store the seed you can somehow sneak it into your wedding vows, write a song where beats correlate to 1s and 0s that spell out your seed in binary. Whatever it is, come up with some definitive way to remember it.
When uploading your product pictures, follow the chapter Uploading images securely from the DNM buyer bible.
How safe is it to use an internet connection at home for vending?
There several complaints where law enforcement analyzed the timing of the Tor usage coming from the suspected vendor's home connection along with his times when he was home and the vendor account being active on DNMs. However if that is the case, law enforcement usually already has a pretty strong case against the vendor they monitor that way. Therefore it is usually better to spend your time, energy and resources on other factors that can get you busted more easily (e.g. packaging).
If you want to hide your Tor usage though, you should go with the Whonix setup described in the DNM Buyer Bible since it is hard to chain a VPN with Tails. With Whonix you just need to follow the setup steps from the DNM buyer bible and then install the VPN software on the host OS. So your future login process would look like this: boot host OS → start VPN software (recommended to set it to start automatically) → starting Whonix (according to the instructions in the DNM buyer bible).
Using a public WiFi also introduces additional risks: you would need to travel to that access point every time you want to log in (which allows law enforcement to still monitor your behaviour and correlate it with the login times of the vendor on DNMs) and you for example need to protect yourself against other people that may look at your screen.
It would come in handy in case of an IP address leak though as it would just show that the vendor used a specific public WiFi and not lead right back to your home address. However these are very unlikely when you are using Tails or Whonix with the security slider set to high, plus such attacks usually do not get wasted on (normal) vendors.
If you have the chance to use a WiFi that is not yours without leaving your own house (e.g. an unsecured network belonging to your neighbour), then you should use it. Otherwise stick to your own WiFi and use Whonix with a VPN if you are seriously concerned about hiding your Tor usage.
Packaging
General
This chapter is about how to package the orders you get
properly.
Before you start packaging right away or listing your
products, you
need to work out a packaging process first. To get ideas
for stealth
and decoys you can order from other vendors who sell the
same
product or a similar one and are known for their good
stealth. That
will point you in a general direction and give you some
ideas how to
properly conceal the package content. Do not copy their
packaging
methods.
While you can also use services like Bitcoin Postage to
buy postage
with bitcoins, it is highly discouraged since such
companies are
known to give out their customers information to law
enforcement.
Furthermore make sure you also read this post (as well
as the
comments) about packaging and customs.
Here more information about what to avoid when packaging
from
various sources:
How to package
Depending on what you are going to sell, you should
vacuum seal it at
least once and package it in Mylar too, to avoid getting
the package
seized because of the smell it leaks. If you ship
internationally, a
decoy is necessary because the package will pass through
two
customs (in the origin country and the destination
country), unlike a
domestic package which will go through far fewer checks.
The location for packaging it the first time (like vac
sealing weed) and
the second one (putting it into a MBB) have to be
different because
you do not want to get the outside of the packaging
material to get in
touch with the product itself. Different rooms for that
are also alright.
If the outside is contaminated because you did all the
packaging in the
same room where the product lays around, dogs will far
more likely
hit on the package. This not only means a dissatisfied
customer and a
potential loss for you (e.g. if you reship), but also
increased attention
from law enforcement on your operation.
Note: know how much to frank your packages with. If you
make
mistakes there, the packages may not get delivered to
their destination
but opened by post office workers. That is a recipe for
getting an
investigation started.
When packaging the product, you need to be careful to
not leave any
fingerprints or DNA traces inside or outside the
package. To prevent
that wear at least long sleeve shirts, two layers of
gloves (e.g. first
cotton ones and then rubber ones over that because some
gloves are
too thin and can still leave partial fingerprints), a
hairnet or ski mask
and other clothing that covers your bare skin to avoid
leaving traces
during the packaging. Ideal would be a full body suit
(example)
because it not only looks and feels cool but also is way
better than the
workaround with the clothing described previously.
When you have a rough idea of how you are going to
package your
product, it is very helpful to write down the steps that
you are going to
make. That means write out the whole process in full,
e.g. in steps like
"roll out paper on the table" and "put gloves on". After
you are
finished with that read through it and correct things
while imagining
the whole packaging process.
When that step-by-step guide is ready, make a test run
and package
something that is legal and similar to the product you
are going to
sell. While doing that you will notice thing you have
forgotten in the
guide or things you should do better. Alter the guide
after you did the
test run accordingly. Then send the test package to your
address or
one that you control to see if everything works fine.
After it arrived successfully you can repeat the test
packaging process
again to see if the changed details work and if you can
improve the
process even more.
Note: you have to treat every package carefully and make
sure that
you do not make mistakes when packaging it. Law
enforcement does
not care if you leave a fingerprint or DNA traces on a 1
gram order or
a bulk one, they fuck you either way. Here one example
for a thread
about vending (specifically about leaving traces on the
packages),
which you constantly look out for when browsing DNM
related
forums.
You should also wipe the packaging material (e.g. vac
sealed bag,
MBB, . . . not the outside of the package itself) with
alcohol to reduce
the smell and remove potential traces. So the first wipe
after you vac
sealed the product and the second time after you put it
into the MBB.
Return addresses
You could use real addresses of individuals living in a
rather poor part
of a town. So if law enforcement starts to investigate
they think it is
just one of the drug dealers living there who sends the
packages, and
if the packages gets returned the individual is less
likely to report it to
the police. Maybe using a fake address once in a while
is not bad
either, since the worst case would be that the few
packages you sent
with a fake return address get opened by postal workers
but the
content is not enough to start an investigation. It also
puts a bit less
heat on the real return addresses (the ones from the
poor parts of the
town) the vendor primarily uses.
But keep in mind that you can also cause a lot of
trouble for the
people living under your return addresses. So avoid
picking ones that
for example have a single mother with kids living there.
However return addresses always should be within
reasonable range
of the used mailbox. It is suspicious if the return
address is in a
complete other town than from where it was sent.
Also these techniques are only a way to delay and
disrupt
investigations to a certain extent. You will have to
switch your
accounts sooner or later as described in the General
Tips chapter, if
you do not want to get busted.
Other concepts:
Use a real return address of a business or a shopping
center. But use a
fake second line something like office 58 but there is
no office 58 at a
gym and the post office knows not to return it but will
still put it on
the truck. Another good one is use a fake apartment
number like
apartment 7 when there are only 6 apartments. Same
things USPS will
direct the mail the mail man will see no box. This
method is going to
get burned soon since USPS is cracking down on those
fake/semi real
return addresses.
Another concept is using the the return address of a
P.O. box and
using different names on them as USPS does not cross
check the
name of the box and where it is coming from. So you
could say John
Smith P.O. box 2284 and well it will never go return to
sender since
that does not exist.
Stealth
Every few months a journalist will get the bright idea
to make an easy
story by buying some drugs from a DNM and talking about
how
terrible it is that it was so easy. They often give
detailed photographs
and descriptions of the packaging. Since the journalists
usually end
the article by saying everything was handed over to the
police, these
are certainly not stealth methods that are covered by
security by
obscurity. In the following a few concrete examples.
NOTE: detailed talking about stealth on
/r/DarkNetMarkets and /r/DarkNetMarketsNoobs is not allowed! Please read the rules for details.
Weak stealth example:
A fucking DVD case
https://archive.li/o/sVVd4/https://wwwwwwwwwwwwwwwwwwwwww.bitnik.org/r/2015-01-15-statement/
https://archive.li/o/sVVd4/https://wwwwwwwwwwwwwwwwwwwwww.bitnik.org/r/2015-03-04-xtc-is-xtc/
https://archive.li/o/sVVd4/https://wwwwwwwwwwwwwwwwwwwwww.bitnik.org/r/2015-04-15-random-darknet-shopper-free/
!MEDIENGRUPPE BITNIK
Random Darknet Shopper
29.10.14 | No. 6
ECSTASY 10X YELLOW TWITTER 120MG MDMA
RANDOM DARKNET SHOPPER JUST BOUGHT 10 ECSTASY
PILLS OF FROM GERMANY FOR 48$





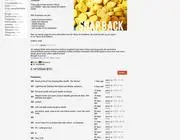
Ecstasy 10 yellow Twitter Pills 120mg Mdma
Ordered by Random Darknet Shopper (29 Oct 14)
for 0.1412554 Bitcoins
Status: Arrived (4 Nov 14)
Shipped from Germany
Item No. 6
The pills were vacuum-sealed in aluminium foil and
placed inside a dvd
case, so they would look like a dvd in a x-ray scan. The
vendor promised
very fast shipping and stealth packaging. Both seem
true. The parcel was
sent from Germany and crossed the border and customs to
Switzerland
without any problems.
Original describtion:
«Beautiful yellow round pills with twitter logo, beveled
edges and breaking line on the
back...»
Medium stealth example:
Ecstasy pill hidden in candy packet
Is your postman delivering drugs?
By Jim Connolly and Anna Doble Newsbeat reporters
5 Jan 2017
Large amounts of illegal drugs are being delivered
unknowingly
by UK postal workers with few checks, Radio 1 Newsbeat
has
found.
For several months we have been investigating drugs in
the post
bought on the dark web.
We heard that "millions of pounds of drugs are bought
online every
day" via the hidden layer of the internet where dealers
can sell drugs
anonymously.
Royal Mail said it does not knowingly carry any illegal
items in its
network.
Newsbeat spoke to delivery staff who said they had
"definitely handled
suspect packages" but there was "nothing they could do".
You can also explore this story in a different way.
Newsbeat
Explains is a new way of experiencing news piece by
piece -
click here to try it with this story.

Image caption:
Packages sent from dark web drug suppliers
to our
reporter
There are fears that users buying drugs this way are
more likely to
widen their substance choices, with dangerous
consequences.
And users we spoke to believe there's a "99% certainty"
that drugs
ordered via the dark web will get to them.
The Home Office says it is spending £1.9m trying to
"increase
understanding" in how organised crime networks
"adapt and diversify"
using technology.

Image caption:
Yvette Cooper visited Newsbeat to see our
findings for
herself
Chair of the Home Affairs Select Committee, and Labour
MP, Yvette
Cooper is looking at how the police can "keep up with
new and
changing forms of crime".
"We need to know there's a proper approach to
enforcement taking
place," she tells Newsbeat.
"One of the things we want to know is how the police are
able to co-
operate with different organisations.
"What is happening to link up [the police] with postal
services or with
customs or with other organisations? What's the
government doing to
lead this?"

Image caption:
Newsbeat reporter Jim Connolly logs onto
the dark web
with Chris Monteiro, an independent cyber-security
expert
How we tested the system
Newsbeat obtained MDMA, cannabis and former legal high, Spice using Bitcoin on the "dark web", a collection of thousands of websites that use anonymity tools to hide their IP address.This part of the internet also contains a marketplace for drugs like heroin and steroids - as well as weapons and fraudulent documents. We accessed the dark web via the Tor browser, free software which conceals users' identities and their online activity from surveillance. Deliveries to a PO Box took around a week to arrive. When they did, we gave them to a government-approved lab for testing and destruction.

Image caption:
An ecstasy pill we bought on the dark web arrived wrapped inside a packet of Haribo sweets
"Unless there are massive raids on markets any time soon" causing "a loss of consumer confidence", this "hidden" drug market will keep growing, says Chris Monteiro, an independent cybersecurity expert and researcher.

Image caption:
The pill was packed inside cling film to make it feel soft
"Talk of better prices and improved purity will continue to spread and eat away at the offline market," he explains. And he adds: "Government and police are more interested in data breaches and weapons [than drugs]."

Image caption:
But there is no guarantee of what you are really buying on the dark web
Waiting for a special delivery
Former user "Steve" tells Newsbeat he bought marijuana, cocaine, ecstasy, and psychedelic stimulants on the dark web.He describes a time he and a friend ordered drugs to take to a festival.
"We were waiting for a package, for an ounce of MDMA to be delivered.
"We see the postie drive down and we get very excited. She gives me the package, I sign for it... happy doo-dah. She had no idea she was a part of the drugs trade
"Steve"
Former dark web drug user "Me and my friend found it incredibly funny how she gave us the post - and had no idea.
"She handed it over and said 'thank you very much' and I said thank you very much.
"She had no idea she was a part of the drugs trade."
What "Steve" did was illegal and could have resulted in a jail term for possession of drugs with intent to supply.
What post workers told us

We went out with a postman who wanted to remain anonymous.
"Patrick" told us that it's illegal for him to open suspect parcels and there's "nothing he can do about it".
"You tell the managers and all they say is you need to deliver it."
He added: "If it's got a stamp on it, you post it. We don't have drug dogs to smell every parcel. We don't have the resources to X-ray every parcel. We just have to deliver it and take the risk.
I've spent 14 years as a postman in uniform and I have never seen a drug dog
Postal worker: "Our job is to deliver it safely to the customer."
Newsbeat has been told that some random spot-checks do occur but most staff we spoke to had never seen a sniffer dog.
"I've spent 14 years as a postman in uniform and I have never seen a drug dog," one worker at a London depot said.
Another said: "You hear rattling of things like pills and assume they're legitimate, but how would we know?"
"I've definitely handled suspect post, but once we have it in our mail bag we have to deliver it," said another.
On a forum used by postal workers we heard from a number of people who all noted that they had handled packages which had smelled of cannabis.
Many described there being more checks in the past when the depot had a customs office on site. Mail being sent within the UK does not seem to undergo the same scrutiny.

Are people trying new drugs because of the dark web?
Yes, according to data from the Global Drug Survey [GDS]."About a third of people said they'd broaden their drug-using repertoire," says Dr Adam Winstock, from Kings College and GDS, who also says "millions of pounds of drugs are bought online every day".
"So it's like 'we've noticed you like LSD and magic mushrooms, perhaps you'd be interested in 2CB or DMT'... "I think there is absolutely that effect," he tells Newsbeat. "You're always worried that an increase in repertoire increases the likelihood that someone comes across something that might be harmful."
One in five people who responded to the 2016 Global Drug Survey said they had bought drugs on the dark web - or had friends buy them for them.
Are any countries tackling drugs in the post?
In New Zealand more has been done to stop drugs in the post."New Zealand is an anomaly in that only 2% of those who took our survey said they'd bought drugs on the dark net," says Dr Winstock.
"The reason people don't go shopping on the dark net in New Zealand is because there's really good co-operation between the police and the postal services and their borders are unbelievably good."
This more joined up approach has led to New Zealand's customs service seizing three times as many suspect packages over the past two years.
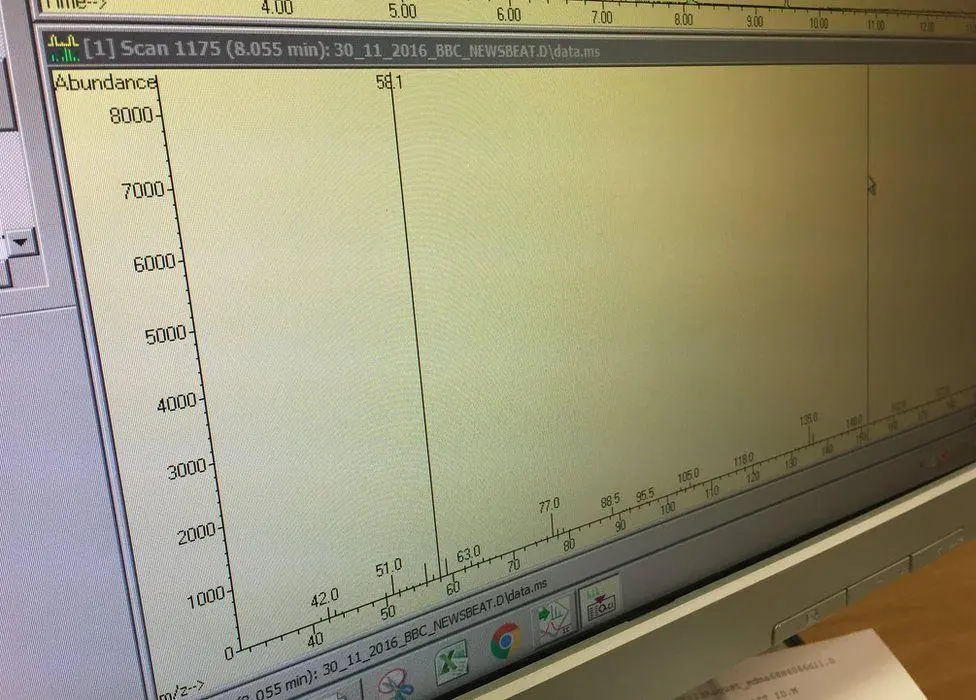
Image caption:
We bought an ecstasy pill on the dark web for £5 plus £3 postage. Tests found the pill's only active ingredient was MDMA.